Top IT Network Security Devices
Top It network security requires the guarantee of restricted access to confidential information, the protection against unauthorized access, risks, and possible security threats, and improvement of network capacity. It is important to protect the network at all its points of access, and the key factors at the top it network security include encryption, secure keys, antivirus software, and sophisticated the top it networks security devices. The Top IT security network is essential for the proper operations of the computer network and here some introduced devices will help your secured network.
Related
Most Effective IT Network Security
There are several top IT security network devices available:
- Active devices include firewalls, antivirus scanning devices, and content filtering devices, which block the surplus traffic;
- Passive devices include intrusion detection appliances, which identify and report on unwanted traffic;
- Preventative devices include devices assessments, which scan the networks and identify potential security problems;
- UTM devices include firewall, content filtering, web caching, which serve as all-in-one security devices.
How is the IT security network set up?
Top It Network security incorporates several layers to the physical and logical perimeter of the system. Each layer of data security controls implements network and controls. Entitled users have access to network services, but users with malicious intent are blocked from accessing these resources.
What advantage do I get from the IT security network?
Digitalization has dramatically changed our culture. Today, how we live, work, play, and learn has all changed. A business that wishes to offer products and services must secure its network. Top It Network security protects from hackers and data breaches. Ultimately it preserves your name.
Some IT security network devices you need to know
Use the appropriate IT security network will effectively guard the network. Here are the most popular forms of IT security network devices that you can install on your network to help protect it against external attacks.
1.Firewall
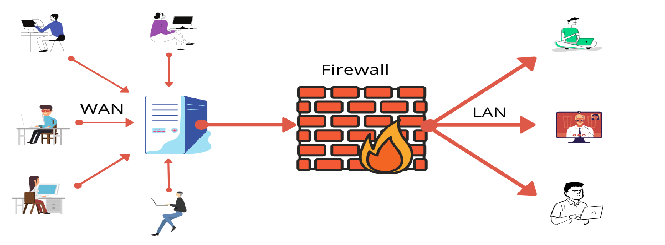
- A firewall is amongst the first lines of IT security network devices in a network environment since it protects a system from another system. Firewalls can be built into routers and servers. There is several the top It network security equipment available today which can perform the same function.
- Firewall as an IT security network device protect networks by preventing intruders from getting in. After firewall rule evaluation, traffic might be allowed or not allowed. There are two different types of firewall protection policies.
- White Listing -The firewall does not let in any connections, except those that have been explicitly marked as acceptable. There are four categories of firewalls which are as follows: firewall, packet, stateful, and web server firewalls.
Packet Filtering Firewalls
- Packet filtering effectively establishes a checkpoint at a networked router or switch. The firewall can examine the data packets without opening up the packets. If knowledge packets are not approved by the architect, they are discarded.
- The positive thing about these firewalls is they are lightweight and efficient in space. These are trivial tasks that won’t change how the machine works, and are pretty straightforward. But they’re still surprisingly simple to circumvent compared to firewalls with more thorough inspection tools.
Circuit-level Firewalls
- Circuit level IT security network device is faster because they search the TCP handshake so they can quickly and easily accept or deny traffic. The TCP handshake is a tool for ensuring a valid Internet session.
- As effective as this firewall is, it does not search the packet itself. If a packet had an adequate handshake but had malware . . . This is why complex firewalls are essential for businesses to defend themselves.
Circuit-level gateways.
- An example of a conveniently implemented firewall used to rapidly and easily accept or reject traffic is a circuit-level gateway that authenticates the TCP handshake. The TCP handshake protocol is a method to confirm the legitimacy of a network session.
- As effective as this firewall is, it does not search the packet itself. If a packet had an adequate handshake but had malware . . . This is why complex firewalls are essential for businesses to defend themselves.
Stateful application firewall
- This IT security network device incorporates both packet inspection technologies and TCP handshake authentication into a higher degree of security than either technology alone.
- These firewalls do put more of a burden on system resources, but then they take up more space. This can slow down legal packets over the slower alternatives.
- Proxy firewalls redirect incoming traffic between the network and the traffic source at the application level, thus, meaning they are called
Application-level firewalls (ALF)
- The IT security network device is distributed by a cloud-based or proxy solution. Rather than making the data packets flow freely, the proxy firewall first creates a link to the source of the data packets and then examines the packets themselves.
- This check examines packet traffic entering and leaving the firewall as well as the TCP handshaking protocol used. Firewalls can scan the contents of the knowledge packet, verifying that it does not contain malware.
- Once the search has been completed, the proxy sends it to its destination. This links your clients and your network stealthy and anonymous.
- Unfortunately, proxy firewalls have certain setbacks such as speeding up the networking process because of the intermediate steps in the data packet transfer process.
Digital integrated firewalls
- Many firewall devices being sold now are said to be state-of-the-art. However, there is not much uniformity in regards to defining a “next-generation” firewall.
- Firewall architectures of the next generation include deep packet inspection (DPI), TCP handshake checking, and surface-level inspection of network packets. Firewalls will also include other web protections such as IPS.
Software Firewalls
- It includes some kind of IT security network devices that are set up on a device or system in the local area (or a cloud server). A benefit of software firewalls is that it is used as a protective layer against various network endpoints.
- With regards to individual software firewalls, managing them can be challenging and very time-consuming. Also, using a single software firewall may not be sufficient for every system on a network, which may entail needing to implement more than one software firewall to protect every asset.
Hardware firewalls
- Hardware firewalls are physical products that act to block data packets and traffic before it’s sent to the network. Physical appliance-based firewalls such as this, are very capable of perimeter protection by stopping traffic coming from outsiders to the networks and endpoints.
- Hardware-based firewalls are not entirely secure. Some could have featured more limiting on the number of links than others.
Cloud-Based Firewalls
- Firewalls may be sold as cloud solutions, or as a service, and are also considered a firewall-as-a-service (FaaS). Cloud firewalls are considered synonymous with proxy firewalls since they are often found in proxy firewalls, and because proxy firewalls are sometimes used along with cloud firewalls.
- The major value of using cloud-based firewalls is their simple scalability for your enterprise. With each new need, upgrading the capability of the cloud server is possible. Cloud firewalls, including hardware firewalls, are cost-effective at securing the perimeter.
Web application firewall (WAF)
- Web server firewalls use a series of guidelines to protect against a client’s HTTP interaction. Applications are online, which need to be connected to the internet for this purpose. This means attackers will target various vulnerabilities within the program, leading to specifically targeted database and website attacks.
- Proxy firewalls only defend clients but WAFs mostly protect servers. Another benefit of WAFs is that they track DDoS attacks in their early stages and can withstand the volume of the threat.
2.Wireless intrusion prevention and detection system (WIDPS)
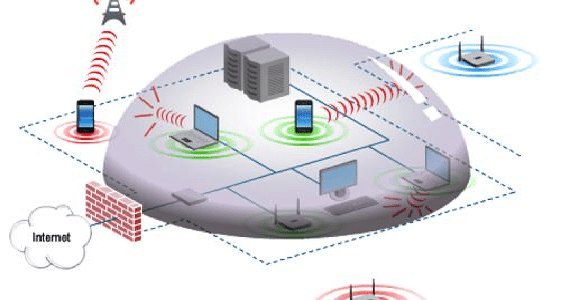
- A WIPS IT security network device has a dedicated surveillance station that searches for rogue access points and other security issues on a wireless network.
- The Monitoring Agent (MA) monitors and provides the management team with information about suspicious access points. To stop MAC address spoofing, high-end WISP surveillance equipment can monitor special radio broadcasts and block spoofed wireless signals.
- If you find the rogue wireless connection in the vicinity, you can selectively disable the signal of this wireless. WIDPSes provide an important layer of security for wireless LANs. A WIDPS is a feature that applies to the Data Link layer of the OSI model.
There are three different ways to deploy a Wi-Fi network:
- The wireless access point constantly checks for illegal wireless access points.
- A camera in the wireless access point constantly searches for unauthorized wireless access points.
Sensors are strategically installed in a building to identify radio frequencies. The sensors capture data that are sent directly to an archival server. The high-end solution is more costly, but it is often seen as being more successful.
Most WIDPS have any of the following:
- Information collected from sensors and sent to a central management server.
- Sensors communicate with a Management Server, which takes necessary decisions depending on the data.
The system that stores and organizes information gathered by sensors. The console provides a screen for administrators to input and monitors all the WIDPS settings.
3. Network access control (NAC)
NAC IT security network device solutions are a vital weapon used in the modern world as handheld devices and the Internet of Things (IoT) have flourished. New technologies come with their own set of vulnerabilities which pose a challenge for technology security experts.
Fortunately, NAC products are designed to allow a wide number of connections from a variety of networking devices. Without a Network Access Control (NAC) in operation, businesses carry on a tremendous amount of responsibility by allowing workers to use their smartphones and tablets on the local network. A NAC approach requires an effort, but one that proves to be more beneficial later on.
The primary objective of any NAC product is to protect the security and integrity of an organization’s network, including both the physical network and any connected cloud networks. NAC IT security network devices are principally constructive, ensuring they prevent threats from being harmful in some way. To help facilitate incident management, some reporting solutions such as Varonis can help facilitate incident management from one central server.
Vendor or Partner NAC.
To again a competitive advantage, businesses must have the ability to seamlessly collaborate with third parties and partners. The exchange of raw data feeds is often sufficient, but also requires network-to-network integration for a smooth experience.
When it comes to network access controls, the tricky thing is ensuring access to the suppliers and partners without exposing you to new channels of attack. A NAC approach also includes a VPN client for remote users to access services within the network via a protected channel. Both movements can be tracked by the NAC so they can be audited.
NAC for incident response.
Newer products have been developed using artificial intelligence and machine learning technology. This ensures that some aspects of incident management can be automated, simplifying the operation. Instead of looking at reasons why a problem could be expanding, find ways to restore networks to maximum power.
For eg, let’s assume that a hacker gains unauthorized access to a corporate network by compromising IoT devices. The NAC tool will ensure that this system is recognized as being corrupted and it will immediately block its access to restrict the extent of the intrusion.
NAC for BYOD.
To save money, most businesses today are allowing workers to use their mobile computers rather than buy staff members a dedicated piece of hardware. To further protect a network, you cannot fully monitor the equipment that would be placed on the network.
In most cases, the presumption is that all new devices are blocked from the internal network before they follow the procedure’s security policy. Your role requires that you have the authorized NAC client installed to obtain complete access to our internal resources.
NAC for IoT
As workers carry their own mobile devices to function, it will be easier to access the devices. That is not true for IoT devices, which lack the standard user interfaces and also only have proprietary features. Even with NAC solutions, IoT devices will also be used in their access policies.
The system’s main feature is to inventory and tag all unknown devices within the complex network. That way, we will categorize IoT devices into special categories with restricted permissions and capabilities. NAC tools will actively track IoT operations and ensure the computers themselves have not been hacked by hackers as happened in the Mirai Botnet incident in 2016.
4. Intrusion prevention system (IPS)
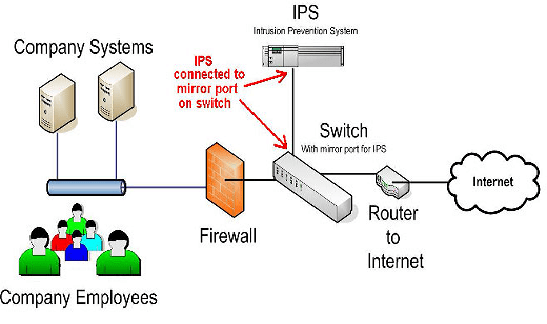
An Intrusion Protection System can track and deter network exploitation by examining network traffic flows. Vulnerability vulnerabilities normally come in the form of malicious inputs to a target program or function to inhibit and hack machines. Then the infected program is not only hijacked but also abused.
Security
The IPS also sits directly behind the firewall and filters harmful traffic coming from malicious IP addresses. The IPS differs from the IDS because it is an adaptive mechanism that takes decisions on the traffic at all times of the day. You must report to the superior (as would be seen in an IDS IT security network device)
Blocking traffic from the source.
A network protection component must function well to prevent deteriorating network capacity. It should be swift and it can be used in near real-time. The IPS must be capable to eradicate risks and false positives (legitimate packets misread as threats).
Detection
The IPS IT security network device uses mostly signature-based and predictive anomalies-based identification.
Signature-based identification is based on special signatures for each exploit. Exploits and ciphers are contained in a large and constantly increasing dictionary. Signature recognition for IPS splits down into two different categorizations:
In this case, exploit-faced signatures trigger exploitation attempts stemming from specific vulnerabilities. The IPS can detect vulnerabilities by searching for an exploitation-facing signature in the traffic stream.
It is a larger signature that accounts for the weakness of the device being attacked. These signature checks help the top It network security administrators to prevent unauthorized access to private networks.
Statistical anomaly analysis monitors network traffic at random and corresponds to a benchmark known for a certain success level. When the baseline network traffic operation conditions have been exceeded, IPS will make an appropriate adjustment to adjust its performance.
It was launched as a standalone unit at some point in the mid-2000s. The new generation of firewalls allowed to provide security well beyond traditional firewalls (at the enterprise level).
5. Intrusion detection system (IDS)
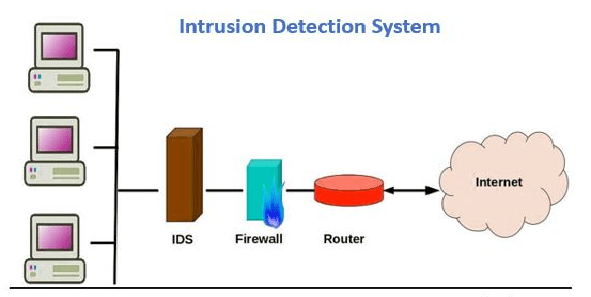
An IDS IT security network device improves the protection of a computer network by identifying a hacker or malicious program, and then removing it immediately to avoid a violation or incident, and then report the results of the incident. Preventing threats would often be less expensive to businesses than countering or remedying the attacks.
So, attackers will succeed in breaching other security mechanisms from time to time. Knowledge about these agreements must be quickly shared with management, and this can be easily achieved with an intrusion detection system.
An IDS IT security network device helps administrators find security holes or security risks that an attacker might take advantage of. There are several intrusion prevention systems:
System-based intrusion detection
Host-based IDS systems are designed to track, identify and respond to various types of malware and malicious activities. Your data will likely be the object of a breaching attack. They will also attack and install Trojan programs in a specific host. Host-based IDS IT security network devices can include decision management, predictive analyses, and data forensics. Host-based intrusion detection systems are useful in combating intrusion attempts in specific files or system facilities. In most instances, host-based intrusion detection is built into the computer system’s operating system.
Connected monitoring devices.
Network traffic-dependent intrusion detection systems monitor network traffic to detect intruders. Unfortunately, firewalls are intrusive tools that intrude through network traffic. The various Internet protocols that manage communications between external and internal networks, such as TCP/IP, NetBEUI, and XNS, are vulnerable to attack and should provide measures that can detect malicious events. Cryptography makes intrusion prevention devices impossible to deal with. There is a limit to speed since 1Gbps will be not required in the operation of time.
Cooperative agents are extremely critical in a distributed IPS architecture. An agent is a separate program that does beneficial activities for humans. An Intrusion Detection System or IDS is a piece of software that monitors files and log-ins and automatically records attacks to a central server. Cooperative agents will establish networks for data transfer and handling. Multiple agents in a network can extract more information about the network than possible with a single IDS.
6. Unified threat management (UTM)
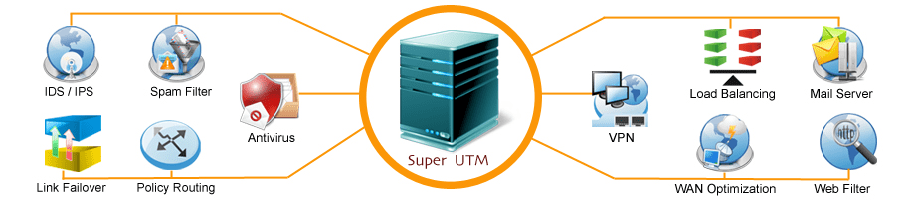
- United threat management is an information technology concept widely termed as UTM IT security network device, referring to a single security solution and, in general, a single security device that provides various safety functions at a single point of the network.
- A UTM IT security network device typically includes antivirus, antispyware, spam control, network firewall detection and avoidance of attack, content filters, and leak prevention. Certain units also provide remote routing, Network Address Conversion (NAT IT security network device), and private virtual network support (VPN).
- The appeal of the approach is focused on consistency, such that individual vendors and equipment can now be assisted by one IT team or division for each different safety mission by all under one vendor umbrella and run from one console.
How UTM IT security network device blocks a virus from a computer — or several
- The advent of combined threats in the industry, combining various forms of malware and attacks that threaten distinct sections of the network, also brought unified threat detection devices to the industry track. It is impossible to prevent these types of attacks using different devices and suppliers for each safety mission, as every issue has to be independently handled and modified to keep up to date with the new forms of ransomware and cybercrime. UTM IT security network device facilitates dealing with various attacks by building a central defense point and having a single console.
- While a centralized approach to threat management problems will resolve some It network security problems, they do not have certain disadvantages, the most important is that the single protection point provided by a UTM device produces a single failure point. This allows certain companies to add a second software-based perimeter to their UTM system to avoid malware from entering or surrounding the UTM firewall.
7. Web filter

- Web filtering is a technology that prevents users of such URLs or websites from browsing by blocking browsers from loading pets. Web filters are manufactured in many forms that provide different solutions for the use of persons, families, institutions, or companies.
- Web filters generally operate in two separate ways. You can block content by consulting recognized lists, which documents and categorize common sites from all kinds of content, according to the quality of the web. Or, you can analyze and block the content of a page live. A constantly updated URL database shows several Web-filter tools to display websites and domains which are associated with hosting malware, phishing, viruses, or other tools.
- Web filters are pretty easy on the surface, but with them, everything gets more difficult as you start learning more. There is no way that any website will be included in exclusion lists of web filters with almost one billion Websites present on the internet.
Customer Base Web Filtering
• Parents – who want to stop their children from viewing material they find unsolicited or offensive – are the three biggest people who use web filtering.
• companies – who want the links to websites outside of their work for workers to be avoided. • Web filters also have useful support to avoid any malware infection.
• Schools – schools tend to apply site filters to companies and parents similarly in the hope that offensive and distracting contents are blocked and, at the same time, they also hope to shield themselves from malware.
Types of web filters
• Blocklist & Allow List Filters – When a parent administrator is used, any websites that are considered inadequate are entered manually in the software, and these websites are blocked afterward. Enable lists can only be used in reverse form – i.e., URLs will then be inserted manually into a permissible registry, and all other pages will be remote.
• Keywords and Content Filters – In many respects, the same kind of filtering is blocking and allows the filtering of a list with a much wider spectrum. Keep a close eye on websites with such keywords or predefined content filters (such as pornography, for example).
8. Antivirus

- Antivirus software as an IT security network device is one of the most commonly used security techniques. There are various ways antivirus solutions can detect harmful programs.
- Based on known malware signatures, it is easy to detect a malicious program. These signatures are essentially a dictionary of viruses, and they can be used by virus scanner programs. The antivirus should be kept up to date to ensure that the new signatures are present. Signature-based identification looks for a certain range of content. Antivirus solutions will compare all data and quarantine something that is some kind of virus.
- By using heuristics — Another approach is heuristics. Heuristics empowers analysts to rapidly recognize previously unknown threats. Heuristics can search a given directory for signs of malware activity that indicate it has been compromised. Administrative authorities ought to figure out how to distinguish harmful programs from normal ones. The threshold must be set at just the right level so heuristics scanning will be accurate. Heuristic signatures are the way of detecting certain forms of “bad” or suspect activity. Per virus is distinctly unique. These attributes help build a security system against viruses. The most common viruses are the clones of old viruses found in circulation almost every day. In this light, there is the logic behind counterattacks against potential viruses.
- Another way of file discovery is using the file length. Viruses function by binding themselves to the host software as their proxy, meaning that the length of the host software normally extends to accommodate the virus. Antivirus software checks to see if any changes have occurred in the file or device once it is used. There’s a virus here.
- Via checksums, we will decide whether the file has been tampered with or not. Checksums could be used to validate files that were fully virus-free the first-time checksums were computed. Symptoms depend on the virus type. You need to remember the symptoms are not specific to any one infection. Any of the most common symptoms may be irritability and depression.
The program often or unexpectedly reboots or restarts.
When technology grows rapidly, the scale increases rapidly.
Adjust file extension (common with ransomware)
- Lost records
- Difficulty saving files
- Too little memory
- Strange sounds or printed text.
- Antivirus as an IT security network device can be a part of the endpoint defense scheme which includes security solutions such as DLP, AppLocker, content filtering, and other functionality.
- Therefore, an attacker may avoid security items in various ways. Since there are no antivirus providers to recognize it, the virus will be non-existent. Since it can also be caught by antivirus definitions. We can prevent detection from anti-virus software by using different types of deceptive and weird techniques.
9. Network load balancer (NLB)
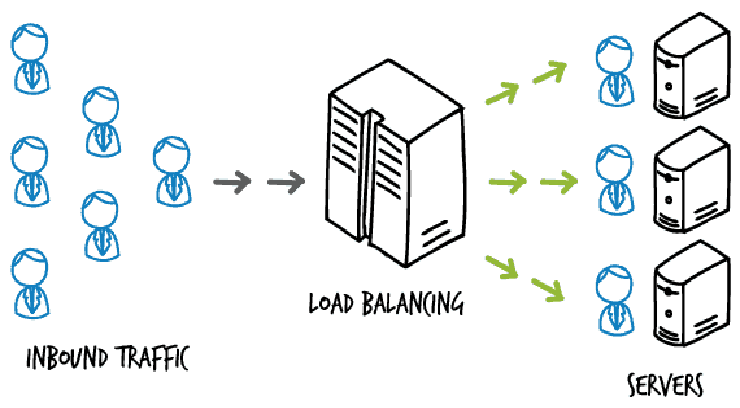
- Network Load balancers are machines like IT security network devices that guide work-related machine processes according to performance-related factors. Organizations are using load balancers to avoid huge computer performance problems and extend the work of the whole network system.
- Software and hardware solutions including load balancers can be added. A load balancer splits the websites travel into different request and are then shuffled until one server becomes available again. The only issue with load balancers is that their tasks must be divided up and allocated to other servers.
There are different ways to optimize the use of computing resources:
- The first client is applied to the first server, the second to the second server, etc. The load balancer starts with the first segment of servers as it reaches the last segment of servers in the list.
Affinity — Affinity reduces customer response time using several approaches to distribute customer orders. There are three kinds:
- No affinity — NLB does not link clients to a specific group of servers; each client application can be loaded with balanced loading to each server group.
- Single affinity — NLB uses the IP address of the client to connect clients with specific server classes. Requests from the same client IP address therefore often enter the same server party.
- Class C affinity — the Class C component of the client’s IP address is used to connect clients with specific server classes. Customers of the same Class C address set therefore still have access to the same server party.
Last link — This approach takes into account the current server load. The latest request goes to the server which currently serves the least number of active sessions.
Adaptive load balancing agent-based — Each server in the pool has a load balancer report agent. This knowledge is used in real-time to decide which server is ideally positioned for a request.
Chained failover – The server order in a chain is set.
Weighted response time — Server health check response information is used to assess which server reacts more quickly at a given time.
Networking software-specific – This technique blends upper and lowers networking layers. It enables users to be informed of the state of servers, the status of their systems, the health of network networks, and the extent of network congestion that is part of the decision-making process for load balancing.
- Network load balancers may be configured actively or actively. An active setup ensures that many load balancing servers are still running on requests. An active-passive setup has one main server and others are ready to listen and to break the load if the first server is overcrowded.
Spam filter
A mail gateway cannot only be used for routing mail, but can also execute other functions like encryption or, to a lesser extent, DLP. Spam filters will more often spot unsolicited emails and block them from reaching a user’s mailbox.
Spam filters judge emails based on organizational or vendor practices or trends. More advanced filters use a heuristic technique to detect spam by suspicious word or word frequency patterns.
The filtering takes place based on certain regulations, including banning emails from certain IP addresses, emails that have certain terms in the subject line, etc. Spam filters are used to screen incoming messages and can also be used to check outgoing messages to detect internal PCs that contain a virus.
Our study indicates that…
We’ve discussed almost all devices that can improve the protection of your home network. Some security systems, such as firewalls and antivirus applications, are essentials to have; but others, including IDSs or IPSs, can be skipped out on. Before designing or investing in a security system, you should always do an IT security risk assessment. Because an assessment would let you know where you should spend your money.
About Writer
AB Rob
Founder & CEO